Our university has a firewall called Demilitarized Zone (DMZ) :). As of now (05/20/2022) when you are on campus and connected to UWyo wifi, you are inside the firewall, but cannot directly access computers on our clusters for some reasons. (i.e. all computers on P&A clusters). You will need to connect to VPN first.
After VPN connection is established, you should be able to connect to our gateway computers: zulu.uwyo.edu and shoshone.uwyo.edu as well as your department PC. You can use the following command to continue. To connect to your department PC, you will have to use IP address directly. Sometimes on MacOS, you might want to -Y flag when you SSH to enable X11 forwarding (give you remote GUI access).
ssh [your username]@zulu.uwyo.edu
ssh [your username]@shoshone.uwyo.edu
ssh [your username]@[your PC IP address]
Note that you will be prompted to enter username and password. The username and password here is not your uwyo NetID and password, but rather the username and password to login into your department PC.
Sometimes it might be a hassle to remember and enter the password every time you tried to login. Here is the Good news: SSH key can help to avoid this process. First, you will need to generate a SSH key and load it to SSH agent. Here is the detailed instructions you can follow.
To let remote machine recognize your SSH key and authenticate your identity, you will need to put the line inside your public key file (the file with .pub suffix. Like something.pub) to the authorized_keys file on remote machine. Usually this file is under .ssh/ directory. You can create one if it is not there.
After these two steps, you should be good to access department computing clusters without a password.
config fileIf you have multiple ssh keys, want to automatically load keys, or want to set up forward X11 or SSH agent, config file can help you do that. Normally the format of the config file consists of several blocks, each block containing the hostname, and then user, the ssh key should use, X11 forwarding, etc. An example is given below. Note that I used * for wildcard options, which means all the options here will be applied first and then specific instruction on different host name will overwrite these options.
Host *
#IdentitiesOnly yes # to prevent trying all ssh keys
ControlMaster = auto
ControlPath = ~/.ssh/control-%l-%n-%p-%r # to generate SSH lock
ControlPersist = 600
IgnoreUnknown UseKeychain # might be important on linux machine
IdentityFile ~/.ssh/mysshkey
AddKeysToAgent yes
UseKeychain yes
Host uwyo_zulu
Hostname zulu.uwyo.edu
User yourusername
PubKeyAuthentication yes
IdentityFile ~/.ssh/sshkey_for_zulu
ForwardX11 yes
ForwardAgent yes
XAuthLocation /opt/X11/bin/xaut
Here are two website for more detailed information.
More practical and examples
Detailed explanations
Usually if you want to use Jupyter notebook on local machine to access data on a remote machine, it is suggested that you spawn your Jupyter server on the remote machine, and then forward a local port to listen to another port on the remote machine. You can achieve port forwarding by the following command
ssh -L [local port]:localhost:[remote port] [your username]@[machine name]
The local port is the port on your local machine, and remote port is the port that your Jupyter is spawn on. Another example:
ssh -L 8891:localhost:8888 neutronstar@gw.uwyo.edu
The person with username neutronstar forwards the local port 8891 to listen to remote port 8888 on the machine gw.uwyo.edu. The remote port (i.e. where Jupyter notebook is spawning at) can be found in the red box
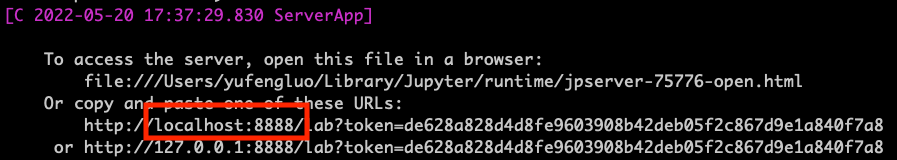
To be continued. つづく